Advanced Encryption Standard (AES) algorithm, its Implementation, Attack Vectors and Cryptanalysis Mitigation
Advanced Encryption Standard (AES) algorithm, its Implementation, Attack Vectors and Cryptanalysis Mitigation
[[ AES history && mode of operation ]]
AES is also known as Rijndael – its original name – derived from its creators, Vincent Rijmen & Joan Daemen. The two developed the algorithm and published it in 1998 during a competition that was hosted by NIST (National Institute of Standards and Technology), to replace its predecessor DES (Data Encryption Standard) which had become too vulnerable and no longer secure to encrypt government data. Attempts were made to secure DES to retain it as the government standard, but the fixes to DES did not last. The last attempt to fix DES was the development of Tripple DES (3-DES), which was an implementation of DES three times.
NIST made AES the standard encryption algorithm under the FIPS (Federal Information Processing Standard) PUB 197 (FIPS 197) in 2001 November. AES is also included in the International Organization for Standardization (ISO), ISO/IEC 18033-3 standard.
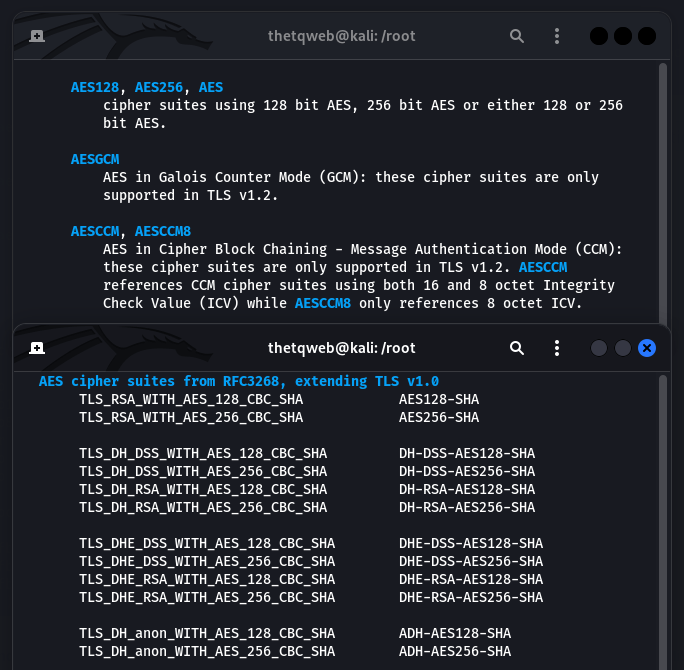
AES operates on a 4 by 4 column-major array of bytes. It is based on the cryptographic concept of substitution-permutation network. For the 128-bit, 192-bit and 256-bit keys used in AES, there are different transformational rounds that convert the plaintext to the ciphertext.
To convert the plaintext to ciphertext, several operations/processes are involved;
1. Key expansion using a schedule algorithm.
2. Mixing of the keys in step 1 with the plaintext.
3. Substitution of the resulting data from step 2 using a substitution table.
4. Shifting rows of 128-bits to the right.
5. Mixing of columns.
All the above steps are collectively called rounds. Each round is made up of the five steps above. Different number of rounds make up different key sizes as specified below:
– AES-128 (128-bit key) uses 10 rounds,
– AES-192 (192-bit key) uses 12 rounds, &
– AES-256 (256-bit key) uses 14 rounds.
These lengths / key sizes above were derived from the published standards although the original Rijndael algorithm was developed to support even more length keys. A set of reverse rounds are applied on the ciphertext to convert it to the original plaintext, and of course using the same encryption key.
For extensive reading on Advanced Encryption Standard (AES)::
> https://csrc.nist.gov/projects/cryptographic-standards-and-guidelines/archived-crypto-projects/aes-development
> https://www.nist.gov/publications/advanced-encryption-standard-aes
> https://doi.org/10.6028/NIST.FIPS.197 (links to the PDF link below)
> https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.197.pdf
[ Advantages of Symmetric-key algorithms (e.g. AES) over asymmetric-key algorithms (e.g. RSA) ]
AES is a symmetric-key algorithm, which implies that it uses the same key to encrypt and decrypt data. The symmetric nature of the algorithm gives it several advantages over popular asymmetric-key algorithms like RSA (Rivest, Shamir, Adleman), also named after its creators Ron Rivest, Adi Shamir and Leonard Adleman. The advantages include;
1. AES requires less computational power to encrypt and decrypt data, which makes it faster than asymmetric algorithms (like RSA). It has been generally said that AES is 1000 times faster than asymmetric algorithms.
2. AES, due to its faster encryption/decryption can be used to encrypt massive amounts of data in reasonable time unlike asymmetric algorithms (like RSA), which are very slow in encryption and decryption such that they operate by encrypting only the key used to encrypt and decrypt data and not the data itself.
[[ Cryptanalysis && AES breaking ]]
Cryptanalysis is the process of analyzing cryptographic systems/algorithms to find weaknesses that can be exploited to deduce the plain text without the decryption key (or to deduce the secret keys used for decryption of ciphers)
As secure as AES is, it has been cracked severally using Side-channel attacks – one of the two possible ways to crack AES – with the other being Brute-force attacks.
1. Brute-force Attack
Brute-force attacks use enormous amounts of computational power to perform try and error on all possibilities to crack AES. These attacks calculate all the possibilities or the whole of the keyspace (all possible key permutations) and try them one by one, with hope of finding the right one.
A brute-force attack on AES is however infeasible (it has been practically tried and tested). In 2011, Fujitsu K, the fastest supercomputer then, could crack a 128-bit AES encryption in 1 Quantilion years (or one billion billion years) which is more than the estimated age of the earth. In 2017, the fastest supercomputer Sunway TaihuLight could take about 885 Quadrillion years to brute-force a 128-bit AES key.
2. Side-channel Attack
Side-channel attacks looks for clues in the computer implementing the AES encryption to minimize the permutations for the key, and thus reduces the time/years required to crack the AES encryption.
The clues used in side-channel attacks include; processor cache tables, audio clues, optical clues, electromagnetic leaks and timing information (time used to perform computations on the computer performing AES encryption).
[[ Mitigation of AES cryptanalysis / breaking ]]
AES is a very secure algorithm, but like any other algorithm, it is only as secure as its Encryption Key and protection of Secrets (keys and passwords).
1. To mitigate breaking of the AES algorithm as a result of weak encryption keys, random password generators can be utilized to secure the key rather than self-created passwords.
2. To mitigate breaking of the AES algorithm as a result of side-channel attacks, constant time principles must be implemented in all instances of code that has any interaction with Secrets (keys and passwords). These principles include;
– Ensure runtime is independent of secret values.
– Ensure code access patterns are independent of secret values.
– Ensure data access patterns are independent of secret values.
For extensive reading on mitigation of side-channel attacks::
Advanced Encryption Standard (AES) algorithm, its Implementation, Attack Vectors and Cryptanalysis Mitigation
Information Security | thetqweb
